OAuth Server¶
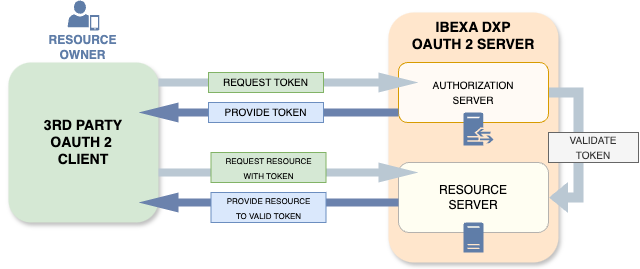
Your Ibexa DXP instance can be used as an OAuth2 server, combining the roles of an Authorization Server and a Resource Server. Client applications, such as mobile apps, are able to authenticate a user, and then access this user's resources.
Server installation¶
Ibexa DXP Oauth2 server package is ibexa/oauth2-server and is not part of the default installation.
You can install it with the following command:
1 | |
Then, in config/bundles.php, at the end of an array with a list of bundles, add the following two lines :
1 2 3 4 5 6 7 | |
Add the tables needed by the bundle:
1 2 3 | |
1 | |
Authorization Server configuration¶
Keys¶
To configure the server, you need private and public keys. For more information, see Generating public and private keys.
You also need an encryption key. For more information, see Generating encryption keys.
Set the following environment variables:
1 2 3 4 | |
Service, routes, and security configurations¶
Uncomment the whole service configuration file: config/packages/ibexa_oauth2_server.yaml.
Tweak the values if necessary.
Uncomment the whole routes configuration file: config/routes/ibexa_oauth2_server.yaml.
In config/packages/security.yaml, uncomment the following three lines under the access_control key:
1 2 3 4 5 6 7 | |
In config/packages/security.yaml, uncomment the three following lines under the oauth2_token key:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 | |
Resource Server configuration¶
To allow resource routes to be accessible through OAuth authorization,
you must define a firewall by using Ibexa\OAuth2Server\Security\Guard\OAuth2Authenticator.
The following firewall example allows the REST API to be accessed as an OAuth resource.
It must be placed before the firewall with a less restrictive pattern like ibexa_front.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 | |
Client¶
Add a client¶
You need the client redirect URIs to create a client.
You also need to agree on an identifier and a secret with the client.
There is only one default scope.
Use league:oauth2-server:create-client command to create a client.
For example:
1 2 | |
Note
You can call --redirect-uri multiple times.
Alternatively, you could add redirect URIs after you create a client, by using the league:oauth2-server:update-client command.
For example:
1 2 | |
Other commands let you list all the configured clients (league:oauth2-server:list-clients)
or delete a client (league:oauth2-server:delete-client).
Note
For a list of all the commands that you can use maintain your clients, in a terminal, run bin/console list league:oauth2-server.
To see usage details for each of the commands, run bin/console help <command> .
For more information, see the package's online documentation.
Information needed by the client¶
Your OAuth2 client needs the following information to be able to use your Oauth server:
- The URL of the Ibexa DXP used as an oauth server
- The client identifier
- The client secret
- The scope (
default)